So i’ve been hosting a modded Minecraft server for my friends and me on weekends. While it’s been a blast, I’ve noticed that our current setup using LAN has its limitations. My friends have been eagerly waiting for their next “fix” (i.e., when they can get back online), and I’ve been replying with a consistent answer: this Friday.
However, exploring cloud providers to spin up a replica of my beloved “Dog Town” Server was a costly endeavor, at least for a setup that’s close to my current configuration. As a result, I’ve turned my attention to self-hosting a Minecraft server on my local network and configuring port forwarding.
To harden my server, I’ve implemented the following measures:
- Added ufw (Uncomplicated Firewall) for enhanced security.
- Blocked all SSH connections except for the IP addresses of my main PC and LAN rig.
- Enabled SSH public key authentication only.
- Rebuilt all packages using a hardened GCC compiler.
- Disabled root access via
/etc/passwd. - Created two users: one with sudo privileges, allowing full access; the other with limited permissions to run a specific script (
./run.sh) for starting the server.
Additionally, I’ve set up a fcron job (a job scheduler) as disabled root, which synchronizes my Minecraft server with four folders at the following intervals: 1 hour, 30 minutes, 10 minutes, and 1 day. This ensures that any mods we use are properly synced in case of issues.
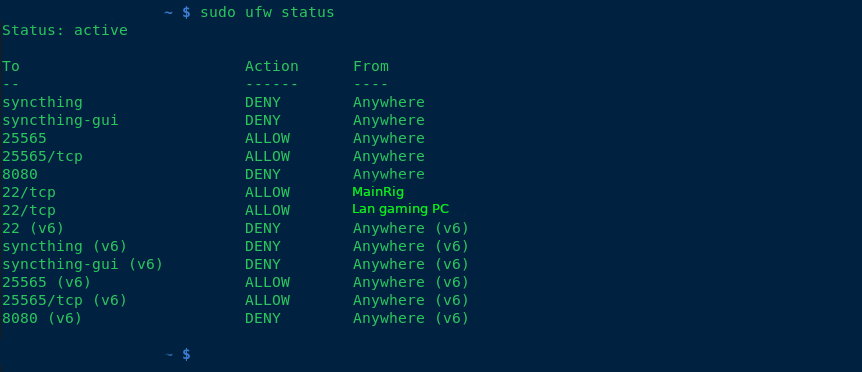
any suggestions of making the computer any more secure, aswell as backup solutions? thanks!
–edit Im using openRc as my init system and my networking plan, is to have dogtown on a vlan via my 48port switch.
–added note, what hostnames do you guys call your servers? I used my favorite band albums and singles for hostnames.
–update Used tailscale, were all addicted to the create mod. And its all been working flawlessly. THANK FOR THE SUGGESTIONS SMART INTERNET PEOPLE!


currently my setup is a dsl modem that goes, to my router/WAP which is a eero, that i plan to eventually replace with a Banna pi R4 which will run openwrt. but as of now the eero goes to my 48 port in my server room, and i have all my computer jacked into that. so to answer your question, my firewall is handled by my router and individual local rules by my machines. im kinda new to self hosting and port forwarding and pfsense looks pretty useful. i know pfsense is based on freebsd so is that a big plus vs openwrt?
please let me know, what some potential solutions could be.
Pfsense is a lot more feature rich than openWRT, especially when it comes to firewall features. Personally I just use openwrt to run my access points.
I would replace that eero unit with an old dell optiplex with pfsense, and forego trying to virtualize PFSense.
Not sure what hardware is in that eero, but if you wanted to keep it as just a basic AP, that isn’t a bad plan.
After that get a second optiplex for publicly hosted stuff. Keep that on a separate port on your PFSense machine, completely firewalled off from the rest of your network via pfsense, only allowing traffic from LAN to your server.
Physically separating your internal network, and publicly hosted services, as much as possible is the goal.
If you can only afford one new piece of hardware, I’d get the pfsense box, and set it up as a wireguard VPN server, disabling the direct port forwards to the VM running Minecraft. Though your friends would need to install a VPN client, and youd have to provide config files.
A used optiplex on eBay usually isn’t much more money to get up and running than most Linux SoC’s after all the adapters and kit is purchased, and they’re usually specced out way better.
Actually if you wanted to do physical DMZ separation, and wireguard you’d really be doing good, but that’s probably a little paranoid.