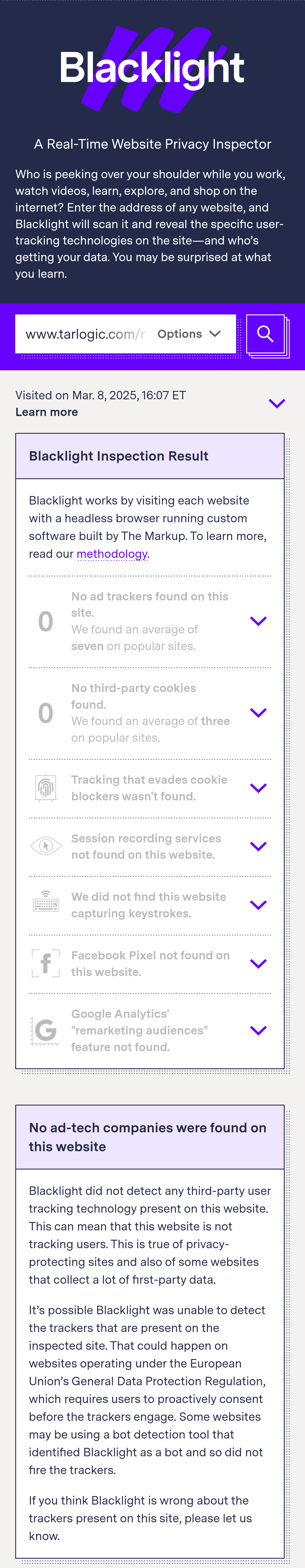
Source Link Privacy.
Tarlogic Security has detected a backdoor in the ESP32, a microcontroller that enables WiFi and Bluetooth connection and is present in millions of mass-market IoT devices. Exploitation of this backdoor would allow hostile actors to conduct impersonation attacks and permanently infect sensitive devices such as mobile phones, computers, smart locks or medical equipment by bypassing code audit controls.
Update: The ESP32 “backdoor” that wasn’t.


This isn’t a backdoor. Just a company trying to make name for themselves by sensationalizing a much smaller discovery.
Seriously this. Every single IC which has digital logic contains some number of undocumented test commands used to ensure it meets all the required specifications during production. They’re not intended to be used for normal operation and almost never included in datasheets.
If anyone’s ever followed console emulator development, they know those undocumented commands are everywhere. There’s still people finding new ones for the N64 hardware
Edit: I should say undocumented behavior, not necessarily new commands