I apologize in advance if this is the wrong community for this post. If so, please point me in the right direction of where I should post this.
I’m thinking of trying out KeePassXC, and, when creating a new database, I came across the following settings:
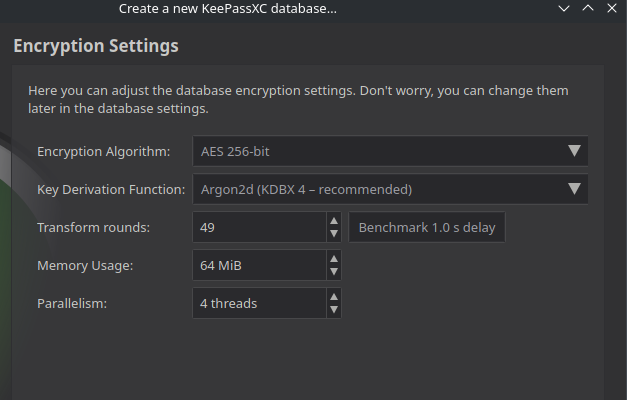
Some of this is somewhat self explanatory to me (“Encryption Algorithm”, and “Key Derivation Function”), but some of it not so much – namely, “Transform Rounds” (I’m assuming that “Memory Usage”, and “Parallelism” are more specific, not to the database on the whole, but, instead, to the decryption itself within the app, or, maybe, even just for the benchmark). What exactly is “Transform Rounds”? Does it mean that the passwords are encrypted over, and over again, in attempt to protect against dictionary attacks? I haven’t been able to find any concrete information.
Those last three input boxes are all parameters to fine tune the operation of the key derivation function, they control the performance and hardware usage characteristics of how to derive the actual database encryption key from your password in order to make it harder to brute force.
The Transform Rounds input essentially controls how much sequential processing power is needed by repeating a specific part of the KDF more or less often, and thus allows you to determine how long the key derivation will take every time. That’s why there’s a Benchmark button next to it - it will automatically test on your CPU and determine how many rounds are needed to produce a 1 second delay on your hardware. Which is an acceptable time to wait for your database to unlock, but bad news for someone trying to brute force your password, as it limits how many attempts different passwords they can test in a given time.
Memory usage controls the amount of memory the KDF needs, and Parallelism controls how many parallel threads are used, both limiting how many parallel attempts at brute forcing your password a potential attacker can run on any given hardware.
Disclaimer: I’m not a security expert, just a software developer who has come into contact with KDFs quite a bit. If I misrepresented anything above, happy for correction!
Great answer, it is similar to the cost parameter for bcrypt/scrypt and iterations for PBKDF2.
deleted by creator
I don’t know anything specifically about KeePassXC but it’s my understanding that a transform round is some computationally expensive task that can be preformed as many times as desired, but must be preformed the same number of times to decrypt as well. The point being to slow down any attempts at brute forcing access to you database if someone gets a hold of your encrypted DB file. For example say it takes one second to derive the proper DB access key from the password you entered to unlock the app, that doesn’t really matter to you logging in as almost no one is going to notice a one second delay in logging in. But if some one else gets a hold of your encrypted password DB then they have to wait one second for every password they try, making brute forcing the DB file practically impossible given you’ve chosen an adequate password.
Ideally you’d choose something which gives a delay not too inconvenient for you when logging in, but enough to thwart the person who might try and brute force the password even if they’re using more powerful hardware.


