- cross-posted to:
- longreads
- [email protected]
- cross-posted to:
- longreads
- [email protected]
This is a very entertaining and educational article, giving insights into the methods used by thiefs to try and get access to your phone data.
I don’t like Apple but it’s great that their security is so good when it comes to this.


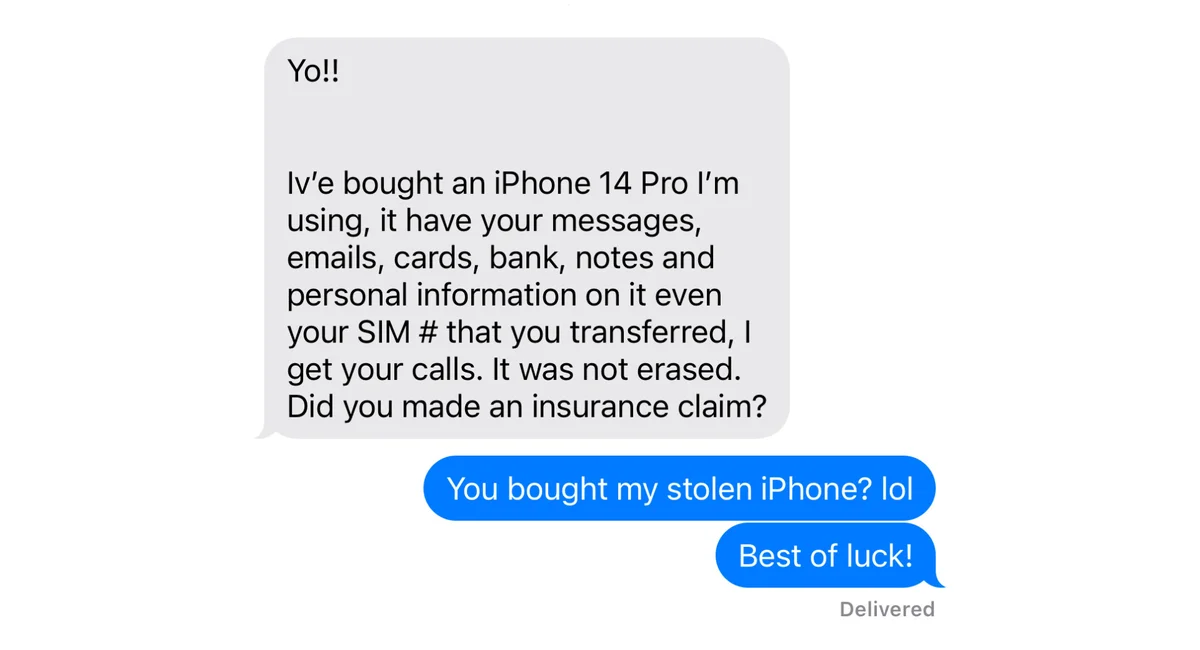
I think when you remotely wipe the phone you can make it show a message with your phone number, in case you’re actually a honest person that found the phone instead of a thief.
In the response posts to the article someone said they got the icloud address via reset request which you can use in iMessage.
Not an i phone person so i can’t verify but thought id pass that along.
That’s interesting, never thought of that as an attack vector.