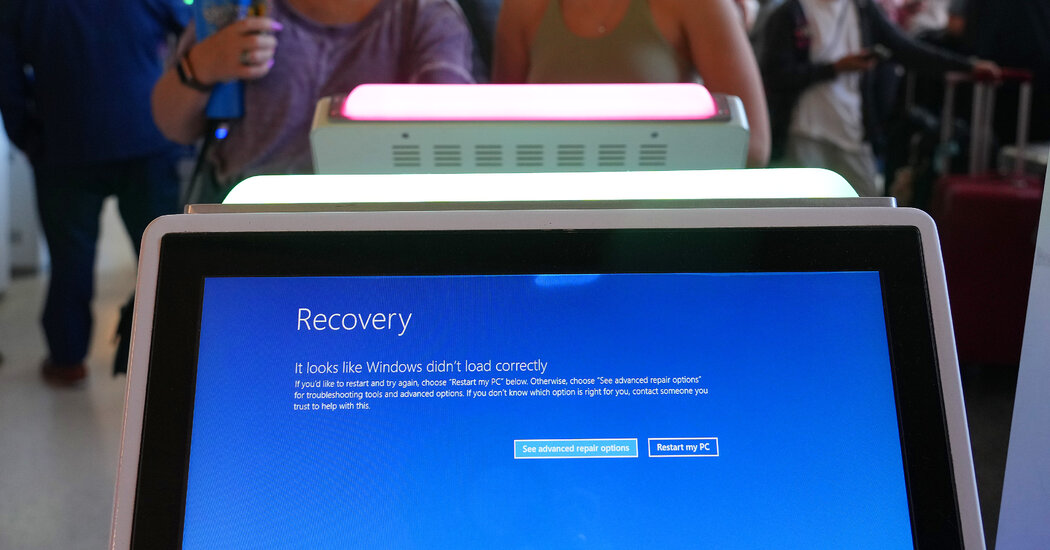
David E. Sanger / New York Times: The CrowdStrike debacle may have accidentally provided cybercriminals and countries like China a more detailed road map to disrupt US critical infrastructure — With each cascade of digital disaster, new vulnerabilities emerge. The latest chaos wasn’t caused by an adversary …
Yeah “target Windows”.
Worse… target CrowdStrike or any other security monitoring system… which means being able to get in anything, Windows, Linux, MacOS… not that they don’t already do that. Because they definitely do.
It had already been done see: SolarWinds
Somehow they are still in business
My point exactly. What good is a dozen docker containers nested in four VMs if you can slap all of it aside with the giant ROOT SHELL hand because you hacked into the remote monitoring software to take control of the system.
The remote management system is now the weaket link in the system’s security chain.
If it’s specifically allowed, yes. Windows is swiss cheese with tons of contaminants in.
Any remote monitoring software is a swiss cheese opening into your system.
Not necessarily. Proper permissions and lack of system bugs are ok to monitor, it doesn’t mean the system is less secure.
Why the fuck does the writer think that state actors weren’t already aware of these vectors?
we’ll do all their work for them, they just need to sit back and take credit the next time we shoot ourselves in the foot …
What do you mean “may have”
Depends on if they already knew this information or not.
Oh, great
way to go a**holes!
Uh, between SolarWinds and XZ and the supply chain attacks being conducted by the NSA that were revealed by Snowden… They already know.
I mean, isn’t this also a problem in other Western countries? Australia got it bad.
Yes, but only country that matters is US /s
Also, they are likely the primary targets (certainly not the only ones) for bad actors.